Ethical Hacking: Enhancing Cyber-security through Offensive Techniques
5 min read

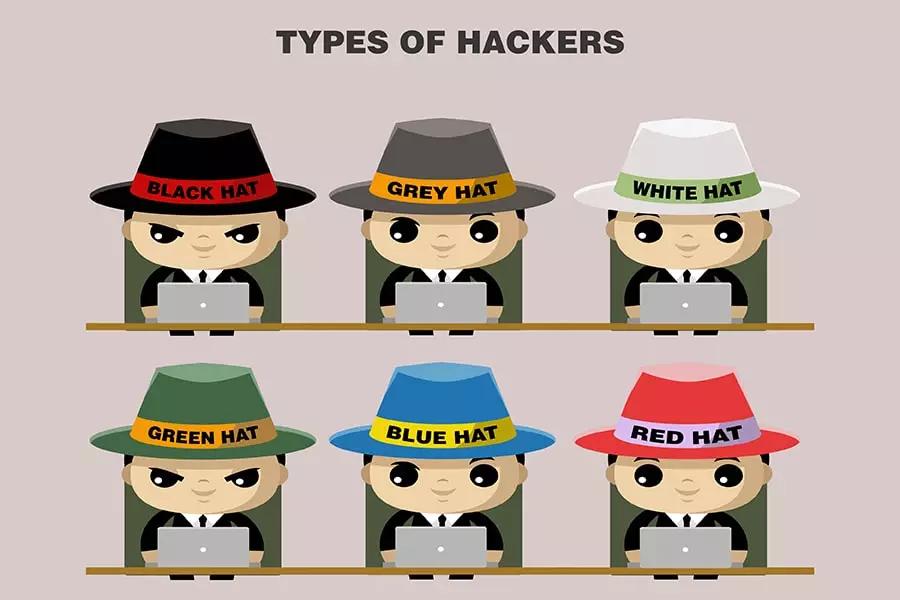
Cyberspace is plagued by a rainbow of hackers waiting to gain unauthorised access to the digital world. There are the Black Hats, Grey Hats, Green Hats, Blue Hats, Red Hats… and to foil their nefarious goals are the White Hats or the Ethical Hackers. The unethical hackers also go by the names of Crackers, Hackers, and Script Kiddies – distinguished by their intentions and the degree of danger they pose to apps and IT systems.
One report places the total cybercrime damages in 2022 at USD 6 trillion, and estimated that over 33 billion accounts would be breached by 2023! Purplesec, a cyber- security company run by U.S. veterans, reveals that cybercrime increased globally by 600 % during the COVID-19 pandemic, and could cost the world $10.5 trillion by 2025.
- The Melissa Virus cost the affected systems $80 million in repairs in 1999.
- 1999 also witnessed a 15-year-old hacking and shutting down NASA’s computers for 21 days, costing the space supremo approximately $41,000 in repairs.
- The 2007 Estonia Cyber Attack was a nation-wide attack and witnessed around 58 Estonian websites go offline, including government, bank and media websites.
- The Sony PlayStation Network Cyber-attack exposed the personal data of 77 million users in 2011.
- The Adobe Cyber-attack breached the data of 2.9 million users and compromised the personal information of nearly 38 million users.
These are just a few of the innumerable hacking related losses and breaches. Today hacking is unfortunately a multibillion-dollar industry with hackers using extremely sophisticated and successful techniques to detect and misuse flaws in IT systems. Hackers are increasingly targeting millions of devices linked to the Internet of Things (IoT). Smartphones, smart devices, webcams, routers, emails, jail-broken phones (where OS restrictions are removed for users to install unofficial apps) – are all sitting duck targets for cyber-attacks and are prone to risks of data theft and corruption.
It is in this cyber-crime ridden world that Ethical Hacking gains immense importance. White Hat Hackers who possess high-tech skills, traits, and techniques identify system weaknesses, to have them fixed before malicious hackers can unleash their damage. Ethical Hacking is thus an authorised attempt to gain unauthorised access to computer systems, applications, or data, by pre-empting the strategies and actions of malicious hackers, in a bid to protect digital systems, devices, networks, and data.
It’s important to understand the various kinds of hacking to provide the right solutions.
- Web Application Hacking – unauthorised access of software over HTTP by exploiting the software’s visual chrome browser, prying with the URI, or manipulating HTTP aspects not stored in the URI.
- System Hacking – accessing personal computers over a network. This is countered by IT security specialists using defensive tactics like password busting, privilege escalation, malicious software construction, and packet sniffing.
- Web Server Hacking – using gluing, ping deluge, port scan, sniffing attacks, and social engineering techniques to access credentials, passcodes, and company information from web applications.
- Hacking Wireless Networks – manipulating wireless network radio waves from a nearby location to illicitly access the system, detect the identifier, and damage the wireless network via network snorting.
- Social Engineering – using deceptive ways to get hordes of unsuspecting people to reveal sensitive information.
- Verifying login security by testing password strength.
- Ensuring security settings and privilege levels in the domain account and database administration by testing out exploits.
- Meticulous penetration testing after every software update/upgrade or after adding a new security patch.
- Safeguarding data communication channels to confirm that they cannot be intercepted.
- Testing validity of authentication protocols.
- Confirming adequate security checks in applications that protect organizational and user databases.
- Defence against denial-of-service attacks.
- Network security and testing of anti-intrusion features.
Ethical Hackers seek to get into the mind of malicious hackers to pre-empt ways in which they could break into digital systems. Their goal is to look for system vulnerabilities and focus on targeting weak spots in the system that can be exploited by hackers. Much like a thief or terrorist, the ethical hacker will first do a thorough recce of the system; gather valuable information to help identify vulnerabilities; use sophisticated tools and testing methods to gain access to the target; and exploit the weaknesses to prove how malicious hackers can unleash an attack.
Ethical Hackers generally adopt the following offensive steps:
- Conducting a Recce
Ethical hackers (like the unethical ones), first gather primary information that’s relevant for attacking the targeted system. This includes data related to individuals, groups, and organisations connected to the target; specifics about the host system; and the target network. Such data helps the hacker plan an informed attack which is solidly backed by clear information on the technology and security levels that protect the targeted system. - Identifying Network and System Vulnerabilities
The next step is to look for weaknesses in the network of the targeted system as it provides easy access. Networks consisting of Wi-Fi or WLAN are used by individuals and organisations to connect to the internet; and organisations additionally use Ethernet connections to link devices in their network. Hackers collect detailed information on the network topology and vulnerable ports, to devise ways in which these can be manipulated to gain unauthorised access to the network connected to the system. - Infiltrating the System
Armed with all relevant data, the Ethical Hacker focuses on breaking into the system by decoding the password or circumventing security measures, to prevent detection. - Retaining Accessibility
After the initial attack, Ethical Hackers leave a backdoor hack in the targeted system to retain access until the job is completed. This ensures easy future access without repeating the aforesaid steps, and is often helpful even if the organisation resets its security measures or releases new security patches. - Covering Up Trails
After the Ethical Hacking is successfully concluded, the final step is to erase all trails. All backdoors, executables, or logs are removed to eliminate the possibility of being identified, or leaving the system vulnerable for unethical hackers. - Reporting
The Ethical Hacker must then prepare a detailed report which clearly documents the system/network weaknesses, and recommend ways in which they can be fixed to alleviate all identified risks.
- Injection attacks
- Broken authentication
- Security misconfigurations
- Use of components with known vulnerabilities
- Sensitive data exposure
| Skills of an Ethical Hacker | Ethical Hacking Protocols |
|---|---|
| In-depth grounding in the principles of information security | Clearly understand the scope and get written approvals to ensure full legality. |
| Proficiency in scripting languages | Respect data sensitivity by complying with non-disclosure agreement. |
| Extensive knowledge of networking | Meticulously report all vulnerabilities and recommend good remedial measures. |
| Expertise in operating systems |
- EC Council: Certified Ethical Hacking Certification
- Offensive Security Certified Professional (OSCP) Certification
- CompTIA Security+
- Cisco’s CCNA Security
- SANS GIAC
Interested in Ethical Hacking but not equipped? Take the first step with PathGlow – your stepping stone to a future in Software Testing, and your link to Ethical Hacking.
Visit us at www.mypathglow.com. We have an awesome Full Stack Software Testing Course that gets you industry-ready in just 3 months! Sign up and benefit from our ISTQB pattern syllabus, training by industry experts, real work simulations, and use of cutting edge tools and methodologies. With our 100% placement assistance, your career will take off to a smooth start.
- Introduction to Data Testing
- Grooming Your Software Testing Talent
- Ethical Hacking: Enhancing Cyber-security through Offensive Techniques
- The Future of Cyber-security: Emerging Technologies and Trends
- Mastering the Art of Ethical Hacking
- Full Stack Software Testing Excellence
- Future of Software Testing in India
- Software Testing Influencing Every Industry/Business
- Guardians of the Software Galaxy
- AI & ML Driving Software Testing
- Software Testers Powering the Digital World
- Software Testing – A Front Runner Career Choice
- How to Become a Software Tester
- The Tale of Two Testers






PathGlow Edulab is indeed your right and radiating path to success, because you learn all aspects of Full Stack Software Testing; get career assistance; gain confidence from practical training; and get placement too!













